Email & Collaboration Security
Endpoint Security (EDR + NGAV)
Today more than ever, endpoint security plays a critical role in enabling your remote workforce.
Harmony Endpoint provides comprehensive endpoint protection at the highest security level, crucial to avoid security breaches and data compromise.
Complete Endpoint Protection
Preventing the most imminent threats to the endpoint
Fastest Recovery
An API-based solution that catches what everyone else misses, including ransomware, account takeover, BEC and supply chain attacks
Complete Endpoint Protection
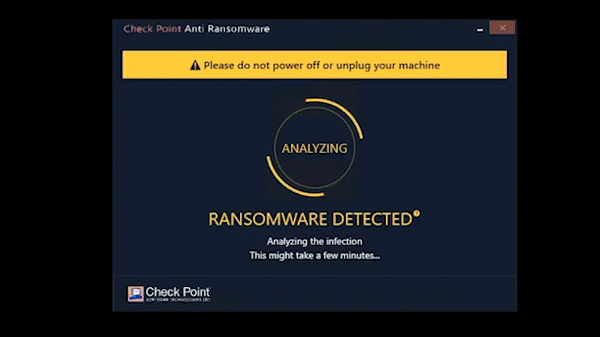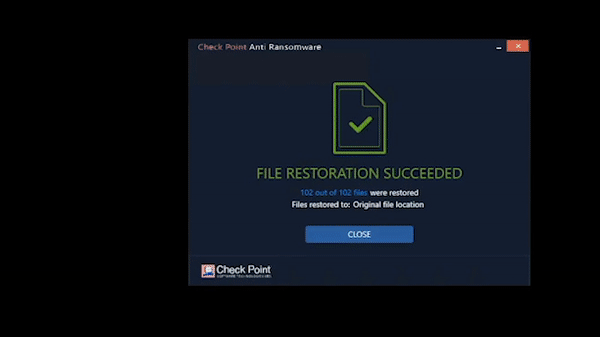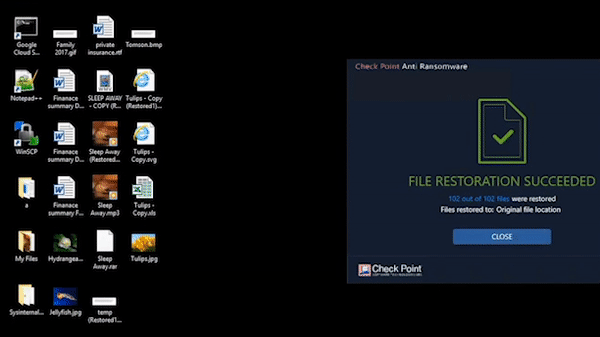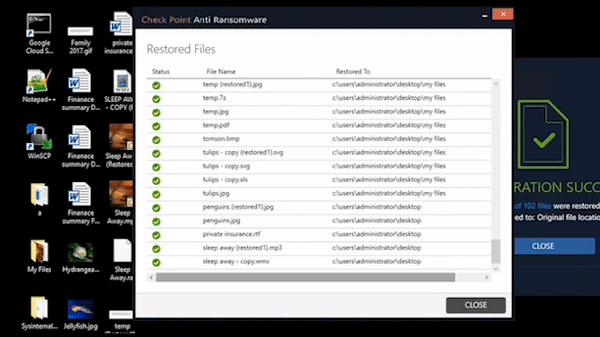
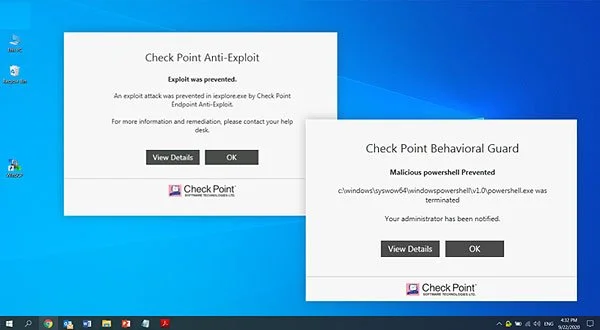
Anti-Ransomware
Harmony Endpoint identifies ransomware behaviors such as file-encryption or attempts to compromise operating system backups, and safely restores ransomware-encrypted files automatically.
Malware and File-less Attack Protections
Threat Emulation & Extraction
Every file received via email or downloaded by a user through a web browser is sent to the Threat Emulation sandbox to inspect for malware.
Files are also sanitized using a Threat Extraction process (Content Disarm & Reconstruction technology) to deliver sanitized content in milliseconds.
Best Total Cost of Ownership
99.2% reduction in phishing attacks reaching the inbox
Blocks 30% more than cloud native security
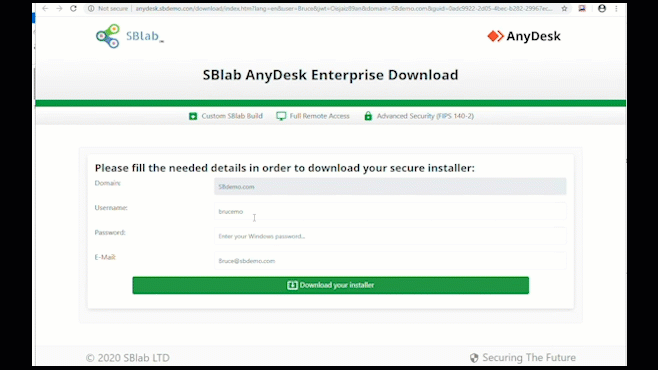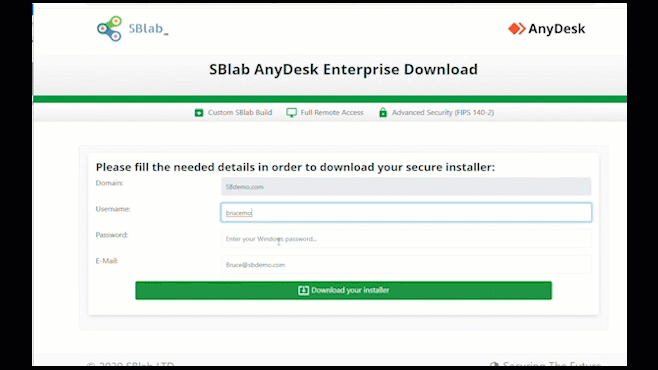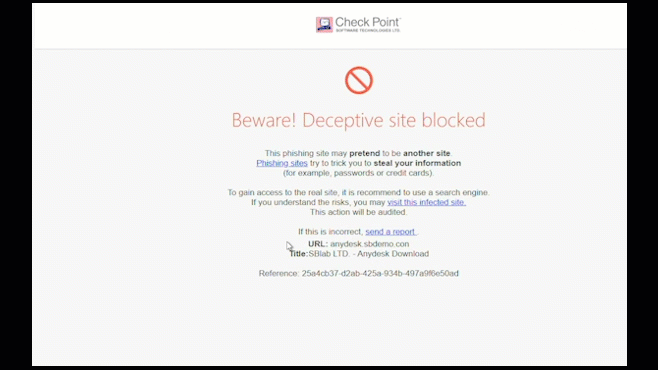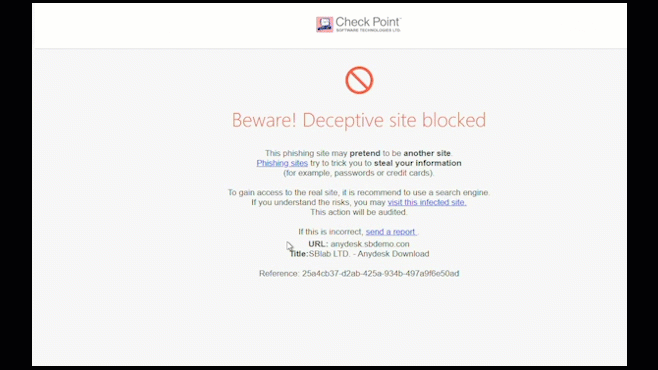
Zero-Phishing
Zero-Phishing® technology identifies and blocks the use of phishing sites in real time. Sites are inspected and if found malicious, the user is blocked from entering credentials.
Zero-phishing also protects against previously unknown phishing sites.
Credential Theft Protection
Benefits of Our Solution
We do not just recommend products—we do the work, evaluate them in our own environment first, perform detailed analysis and then recommend them to our clients. If you have an existing IT team or cybersecurity program in place and are looking for specific tools to compliment or improve security, we can help.
Reduce Operating Costs
A security incident can stop you from being 100% productive at work. This costs the company a lot of money in lost productivity and in opportunity costs. A virus can hit many machines and take weeks to eradicate. Removing this risk will save you money.
Protect Your Company’s Critical Assets and Information
Proactive technologies ensure an additional protection layer against all types of unknown malware, targeted attacks and Internet threats.
A Flexible Security Solution
Our advanced security features offer the appropriate security for any size of company and network.